Thursday, October 9, 2014
click on this link
THis is very importent massage.................................please click on this link if you want free wesite...............
http://VisitsToMoney.com/index.php?refId=552555http://VisitsToMoney.com/index.php?refId=552555
Sunday, March 23, 2014
3 Basic Tips to Prevent A DDoS Attack
Distributed denial-of-service (DDoS) attacks are always in top headlines worldwide, as they are plaguing websites in banks, and virtually of almost every organization having a prominent online presence. The main cause behind the proliferation of DDoS attacks is that there is a very low-cost that the attacker has to incur to put such attack in motion. Fortunately, today various prevention methods have been developed to tackle such attacks. Before delving further into understanding about the ways to prevent DDoS attack, let�s first understand what exactly a DDoS attack is!
Understanding DDOS Attack
A DDoS (distributed denial-of-service) attack is an attempt made by attackers to make computers� resources inaccessible to its anticipated user. In order to carry out a DDOS attack the attackers never uses their own system; rather they create a network of zombie computers often called as a �Botnet� � that is a hive of computers, to incapacitate a website or a web server.
Let�s understand the basic idea! Now, the attacker notifies all the computers present on the botnet to keep in touch with a particular site or a web server, time and again. This increases traffic on the network that causes in slowing down the speed of a site for the intended users. Unfortunately, at times the traffic can be really high that could even lead to shutting a site completely.
There are several ways to prevent the DDOS attack; however, here in this guest post I�ll be covering three basic tips that will help you to protect your website from the DDoS attack.
1. Buy More Bandwidth.
One of the easiest methods is to ensure that you have sufficient bandwidth on your web. You�ll be able to tackle lots of low-scale DDOS attacks simply by buying more bandwidth so as to service the requests. How does it help? Well, distributed denial of service is a nothing more than a game of capacity. Let�s suppose you have 10,000 computer systems each distributing 1 Mbps directed towards your way. This means you�re getting 10 GB of data that is hitting your web server every second. Now, that�s causes a lot of traffic!
So to avoid such issue, you need to apply the same rule intended for normal redundancy. According to this technique, if you wish to have more web servers just multiply around diverse datacenters and next make use of load balancing. By spreading your traffic to various servers will help you balance the load and will most likely create large space adequate to handle the incessant increase in traffic.
However, there�s a problem with this method that is buying more bandwidth can be a costly affair. And as you�ll know that the current DDoS attacks are getting large, and can be a lot bigger exceeding your budget limit.
2. Opt for DDoS Mitigation Services.
A lot of network or Internet-service providers render DDoS mitigation capabilities. Look for an internet service provider having the largest DDoS protection and mitigation network, automated tools, and a pool of talented anti-DDoS technicians with the wherewithal to take action in real-time as per the varying DDoS attack characteristics. A viable alternative is to utilize a DDoS prevention appliance, which is specifically intended to discover and prevent distributed denial-of-service attacks.
3. Restricted Connectivity.
In case you have computer systems that are connected to the web directly, a better idea is to properly install/configure your routers and firewall so as to limit the connectivity. For an instance, while receiving some data from a client machine you can only allow traffic to pass from the machine only on a few chosen ports (like HTTP, POP, SMTP etc.) via the firewall.
Websites are largely getting attacked by hackers every second. Denial-of-service attack is insanely getting huge and is creating a lot of problems for business organizations having strong online vicinity. In this guest post you�ll not only understand what a DDoS attack actually means, but will also come to know about a few type of methods to prevent DDoS attacks. Aforementioned are three tips that I�ll recommend you to run through to at least understand where to get started towards building a resilient web network with chances of surviving a DDoS attack.
Lucie Kruger is a tech savvy writer who works for a leading Android Applications Development Agency. You can also contact her, if you are looking forward to Hire Android App Developers
Wednesday, March 12, 2014
8 Awesome Tips For Freelance Programmers
A freelance programmer can enjoy a nice career. Not only that, he or she can avoid working at a large corporation where they will have to deal with company politics and an eventual ceiling. Of course, it is not all fun and games as a well-trained and hardworking programmer should follow some basic tips if he or she wants to enjoy success in this arena. With that in mind, here are eight tips for freelance programmers.
1. Constant communication:
When taking on a project, one should communicate with the business as often as possible. This means, when speaking to the client, one should mention any road blocks or any accomplishments. With an open door policy, the programmer will have an easier time keeping clients happy and informed.
2. Educating:
While most software developers possess a lot of skills and brains, it is wise to attend more computer classes. By continuing the education, a hardworking programmer can learn more and avoid getting left behind by the competition. In fact, this is extremely important as this field is ever-evolving and new coding ideas and techniques come up all the time.3. Do not sell yourself short:
All-too-often, an independent contractor or business owner will ask for a low wage. When doing this, one will hurt their long-term chances for success. While it is not wise to ask for top dollar, it is beneficial to demand a livable wage. Believe it or not, when dealing with a confident programmer, a company is likely to give in to the financial demands.
4. Home office:
Whether a person works from home or at the office all the time, they should still have a home office. With this, a programmer can complete tasks without interruption from spouses, children or animals. Without a doubt, this is extremely important as a serious programmer will need to concentrate on the task at hand.
5. Have website and online presence:
Now, more than ever, a company owner or contractor should have a website and online presence. With this, a reliable software developer can reach millions of potential clients. At the same time, while making a website, one should keep it simple, straightforward and easy to understand. With this, a programmer can showcase his or her talent for the world to see.
6. Outsource quality assurance:
It is not easy for a programmer to check out his or her programs and code. To avoid turning in a bad product, a smart developer should hire a contractor who can check out the code. By taking a few hours to go over everything, a quality assurance analyst can find any issues and report back to the programmer. This is a great idea as one mistake can result in serious problems in the short and long run.
7. Speak up:
Often, a foolish client will want an unrealistic or impractical solution. While the customer is always right, it is still beneficial if a programmer voices his or her concerns. This should not cause a lot of problems as most business owners will willingly give in as they will, usually, trust the programmer. Either way, it is wise to remain assertive when talking about the product.
8. Set schedule:
It is often tempting for a business owner to set a weird schedule or work nights and weekends. While this is okay at first, a serious programmer who wants to succeed should opt to work a typical 9-5 schedule. This allows other business owners to stay in contact and communicate with the programmer. Since most other entrepreneurs love to work 9 to 5, this is a great way to go above and beyond and offer solid customer support.
It is not easy to work as an independent software programmer. With that in mind, with a few basic tips, a developer can take his or her ideas to the next level. Remember, when focused and ready, a programmer will please his or her clients and make a nice living in the process.
Robert Cordray is a freelance writer and expert in business and technology. He has received many accolades for his work in teaching solid entrepreneur advice.
Friday, March 7, 2014
Redirect To Any Website Using Google Url
Today i will show you to make google link that redirects you to any webpage you wish. This url will start with www.google.com and followed with some characters and symbols. You can trick users to visit your site by changing your webpage url that look like google. As no one will doubt google. So lets get in to.
Working Demo
Visiting the below link you will be redirected to www.coolhackingtrick.com
https://google.com/url?q=%68%74%74%70%3a%2f%2f%63%6f%6f%6c%68%
61%63%6b%69%6e%67%74%72%69%63%6b%2e%63%6f
%6d&ei=AyQZU6rUAYLChAfagIHgCQ&sa=X&oi=
unauthorizedredirect&ct=targetlink&ust=1394158347029455&
usg=AFQjCNF6M9TeMcIyrfeoCrYSHXyGWuO85w
How To Redirect Any Site From Google ?
1. Go to Google Redirect Exploit2. Enter Your Url in the input box as shown below
3. After entering the url click on submit and Google's url will be generated in the textarea as show below.
4. Now you can use that url and upon visiting that url you will be redirected to your site.
More Cool Google Tricks
Sunday, March 2, 2014
Computer Hacking in the New Age, All you Need to Know about Hacking Today
Every human discovery has pros and cons, so is the computer which has pervaded all our lives. The modern humanity is increasingly dependent on computer for various day-to-day activities. Computers do us a whole lot of good things, but it is not without some pitfalls. With the extensive use of internet for hundreds of our needs, computer opens a vicious cycle of hackers. Computer hacking is a term which refers to an individual�s illegal and unauthorized access to the data which are stored in a user�s system. This is done to disturb the confidentiality and security of the user�s computer.
The hackers focus on individuals� computer system when they are online. As long as you are not connected to internet you are less prone to hacking. The access to internet has actually made computer hacking easy. You must protect your computer with strong antivirus and firewall programs to keep hackers away. Hackers are known for creating problems which are difficult to solve. This gives a good business to computer investigators and technicians. Hacking can be done in lots of ways. Few of them are given below:
- Worms: These are the programs which propagate through networks.
- Trojans: These are hidden in websites, attached files and emails.
- Viruses: These attach themselves to various kinds of files. They can damage certain functions of your computer.
Hackers also crash on wireless networks which do not have firewall installed and enabled. They can also send email attachments with malicious software which get embedded on the victim�s computer. Hackers attack accounts which have weak passwords. All these are done to get access to confidential and sensitive information of the users. Whatever is the method of hacking, the effect is harmful for the user. Your system will be flooded with viruses, malwares which steal your information. In order to avoid hacking one has to make sure that the systems at home or office have the latest anti-virus program and firewall installed and enabled. These programs need to be regularly updated. Use the latest browser and scan your computer on a regular basis.
New Age...
The New Age of internet has brought with it many risk factors along with umpteen advantages. The New Age is the time where our personal lives are no longer very personal, but people are able to access personal information of internet users from various sources in the virtual world. We need to be careful about usernames and passwords, else it will lead to dangerous consequences. Universities, large companies and government agencies are mostly targeted by hackers simply because of the bulk of information they handle. The great newspapers like The Wall Street Journal and The New York Times were also targeted by hackers.
Computer hackers are people who gain remote access to information stored in a system elsewhere. During the 1950s and 60s hackers were more drawn towards learning the operations of a computer rather than stealing confidential information of a remote user. Unlike the olden days, now computer hacking has become more sophisticated and organized. In the late 1990s hackers tried to get access to files in the network of Pentagon. Some more expert hackers gained access to the patent files at the Indiana University School of Medicine in February 2003. Many hackers were sentenced in the history since hacking represents a potential national security threat.
Viruses
One major tool hackers use to steal information from computer systems is the use of viruses. Over the years the number of viruses has increased drastically. The virtual world now has above 100000 viruses and the number grows virtually every day. Apart from the threat the computer hackers pose, they also can be beneficial in one way. They can bring to light the flaws in a computer network. Hackers can help in redesigning the system and in making information inaccessible to illegal users and to unauthorized access.
Getting Administrative Access
Getting a log in password is one of the predominant ways to get access to a computer which is by the side of the hacker. Getting remote access to a computer is another way to hack a system. Managing to crack a Wi-Fi password is the third method of sneaking into someone else�s system. Hacking if done on a public or school computer will have serious consequences. The hacker will be put behind the bars for illegally accessing the computer which does not belong to him or her.
Tuesday, February 25, 2014
Build Your Own Games, Become A Programmer
Video games are a blast to play! Wouldn�t it be great to have a part in creating them? But where do you start? For a gamer, being able to take part in creating games would be like a dream come true. Let�s look at a few facts about the gaming industry. In 2012, the gaming industry accounted for $20.77 billion in revenue including hardware, software and accessories. Most of these companies were based in the United States. More detailed information can be found here.
So, we have an enormously large industry and most of it is located right here in the United States. There is no reason why a person with the desire and discipline cannot make their dream job a reality!
The following are some steps to help get you out on the path to your future in gaming. The best part is that most of these options are free. But do require some discipline and effort... and practice, practice, practice!
Be informed, educate yourself
There are some major sources of information online regarding the gaming industry. Become involved with these websites. join in on discussions in the forums and even try to contact individuals from the forums that seem willing to be helpful to newcomers. These sources can be invaluable in learning what trainings and skills are a must for someone to become a professional. A few industry online publications are Gameslice and Gamasutra.
Determine what skills and knowledge you now possess
Begin gathering information about the types of games you wish to program. Having a firm grasp on the games you like to play and programming languages that were used to make those games will begin to steer you in the direction you need to go. Programming, also known as coding, can be difficult in the beginning. Luckily there are many web sites on the internet that offer free learning tutorials for beginners in any language you can imagine. It is recommended to start with some of these free tutorials just to get your feet wet and get you used to the vocabulary of the industry. Check out below article to learn programming.
Get to know commercially available game engines
Most games have a game engine. The game engine is kind of like the foundation that the code works with to create the desired effect within the game. Most of these are available freely either with a game or can be downloaded. You may have heard of some of them: Unreal, Crysis, Source, FrostBite and Creation are just a few of the larger ones. Discover which game engine your favorite games run on and play with the engine yourself.
Take a Coding Class
This is where it all begins to get real. You need some official coding classes. As a starter, consider a course in DarkBasic. DarkBasic is one of the most recommended beginner languages. At this point you should also consider taking a course in Microsoft Visual Basic. A good knowledge of Visual Basic will provide you with the understanding of how code works with Windows operating systems. There are numerous schools whose sole focus is coding. Research the ones who are interested in and to go back to the forums, or individuals you met there and ask their opinions. Then make your decision and register for the classes.
Develop a problem-solving attitude
It cannot be stated more strongly how important a problem-solving attitude can be in game development. You really have to love solving problems. The larger part of coding is developing the code itself. The second largest part of coding is solving all of the problems with the initial code that you developed. You will be spending a large portion of your time resolving problems in your code... So having a problem-solving attitude is crucial to your future career.
Robert Cordray is a freelance writer and expert in business and technology. He has received many accolades for his work in teaching solid entrepreneur advice.
Wednesday, February 19, 2014
Downloading Torrent Using Internet Download Manager

Hello friends, today i will show you the way to download torrents with Internet Download Manager. Torrent is tiny file with .torrent extension which allows you to download huge amount of data. We use torrents to download various stuffs like movies, games, software package and plenty of different things. you'll transfer torrents from several website. The transfer speed for torrents depends on seeds it has. It will make difficult for you to download files with very low or no seed counts. However with the assistance of this trick you'll be able to download torrent file with IDM. This tool can be really helpfull when you want to download file that has very low seeds. IDM is the quickest file transfer manager on the internet market. So lets begin!
How To Transfer Torrent With IDM
1. First download the torrent file with .torrent extension which you wish to download from the internet directly without any torrent client like utorrent.2. Now open zbigz.com and you will land on its homepage.
3. Then Click on upload Torrent and browse your torrent to transfer and click on Go.
4. Then it will ask you for Free or Premium service, choose Free to proceed further.
5. It will take some time to cache your file. Once the caching is done, click on transfer button to download your file as shown below.
6. You should have internet download manager installed on your computer so that download start inside IDM. If you don't have IDM don't worry it will download directly.
Note: If you decide on to use Free transfer then you wont be able to transfer file of more then 1 GB
More Awesome Tutorial
Vikrant Thakur is a computer science student from Himachal Pradesh in India. He loves to share his knowledge of computer and web technology with other. Connect with him on Facebook
Friday, February 14, 2014
Fraudsters Shall Not Pass - Simple Advices On How To Avoid Scammers In Social Networks
Social networks are always great for communicative people; they make you closer to your friends, relatives and hackers. Social networks are very attractive for such kind of people. You can ask me: �Why do they need that?� All they need is your account. The fraud schemes may be different. But the main aim of them is money. They can ask your relatives for help, especially when you�re far away. Why shouldn�t they believe their own child, when he needs money?
Fraudsters do not disdain playing on the heartstrings. They can write everything, that there�s an accident, you�re in a hospital, etc. So today we�ll study to confront fraudsters and keep our nerves and money safe.
Consequences
The most people don�t think about possible risks when creating their profile on social networks. The more personal and professional information you give, the easier it is for fraudsters to rob you. Let us discuss the easiest scheme. Some criminals are simply searching for people living in the same city to plunder their houses. Why does it happen? Different people are writing perfect information, like �We�re going to visit California next weekends. Hoping it�ll be great� Of course it will be great. For the robber, because now he knows that the house will be empty during weekends and it�s the perfect opportunity for him.
The second thing is the photos. When you�re downloading images and photos on social networks not only your friends like them. It�s also the perfect resource for burglars. From home-made photos, they can receive information about your welfare and house structure. When you have a dog, the robber will be prepared, because everyone has photos with their home pets. That�s why we earnestly advise you not to put in the Internet photos of your house, and some things that can attract robbers, for instance your new car or a brilliant ring.
Advice
The next our advice � create a complicated password. We�ve just discussed what fraudsters can do with the access to your account, so try to protect yourself, your friends, and relatives as good as you can. Don�t make a password consisting of just your birth date. Remember, that it�s the first combination fraudsters try. Also, don�t put your birth date as the answer to the test question if it�s mail. Check out below article on password cracking.
Let us imagine that you have a complicated password, you don�t download the �rob-attractive� photos and one day you receive the link from your friend where he asks you to vote for him. Stop now. This can be a trap. If you�ll link, the fraudsters receive your personal data, such as login and password. Such scheme is called �fishing�. So, in this case, ask your friend something personal. The other variant is just to make him a call and ask about this. If you�ll receive the answer like �What are you talking about?� you should explain him that he was hacked and offer to change the password. Check out below tutorial to know about popular hacking method used to acquire sensitive information about oneself.
Phones are really helpful things. Explain to your friends and relatives that you can be hacked and if they receive messages with money requests, they must call you at first and ask about that. Remember that your security is in your hands and be careful.Wednesday, February 5, 2014
Hacking Someone's Facebook Password Using Some Software Or Website? No Sir You Can't!

Do you know there are over thousands of websites and software that claim to hack Facebook password of any account? They'd ask you the victim's profile ID, maybe your credentials and some money too and will reportedly tell you the password which, to be honest, never works. Ever wonder why? Let me tell you why, they're FAKE! They're a scam which tricks you somehow in losing your money or your own Facebook account. Just give it a thought, why would Zuckerberg and his team spend Billions of Dollars on Facebook if one could hack it in less than a minute? Today, we'll take a look at this topic in detail with some example websites and software and get answers to some common related questions.
Back in 2005, I came across a mechanism that reportedly hacked Yahoo mail password for a user using some simple tricks. It didn't work for me for obvious reasons but I didn't stop believing the possibility until I grew up to realize how helpless I am here. One of the major concerns of large organizations like Facebook and Yahoo is security because of the super sensitive information about people they have. Several hundred million dollars are spend yearly by these organizations to ensure security and then there's these websites that claim to undo all that protection in less than a minute.
The Facebook password cracking Websites and Software
Let's start with some examples here. I googled the subject and picked the top results without order. Didn't care to search harder because there are thousands such and I know that all are FAKE.
So let's look at this GETFBHACK.com.

Their FREE Facebook hacker program is said to be capable of cracking the password of any Facebook user within a day. Sounds cool, I could try it out, but my Norton Antivirus rejected the file straight away.
I also picked up another one. This Hack-Fbook-Password asks me to enter the profile ID of a user and it will crack the password. I said Okay and began the process.

It ran certain algorithms to determine the password and finally landed me on a page that said I could DOWNLOAD the password IF I fill an online survey first. Those of you who've been redirected to surveys would know they don't work and are put just so to get traffic and earn money.
I said maybe I should leave the website now but hey, they gave me a prize!

So I just became the luckiest person in my city just like that!
Now tell me, how can a sane person believe in all this?
The truth!
Let me get this straight to you, these websites do nothing at all just waste your time and are never able to do the job. In fact, downloaded programs just make the situation worse when you run them. I had my Norton Antivirus to guard me otherwise I could be in severe danger currently.
These software are mostly keyloggers and tracking programs that record your keystrokes and action and steal personal information from your computer in the background and send it to their master servers. So ultimately a hacker wannabe gets hacked, how ironic!
From now on in the post, I'll be using the word 'Hacker' for these websites and software since you're no more in the position to be called that.
Why do these 'Hackers' do all that?

Setting up websites, maintaining them and developing software is not an easy task. It requires some money. So why do these 'hackers' do all the hassle? It's because they get equivalent or more money in return. They can extract your credit card details and other banking info from your system and use it for their advantage. They can hack your account and use it for wrong purposes. Give me one reason why one wouldn't steal money and hack accounts for no loss.
Why people fall in their webs?

Why do people try to use such unreal hacking procedures? It's because it's unreal to me, it's unreal to you but not to those who are not much familiar with the working of a software. They get in the web of these hackers and eventually get screwed up pretty bad without consent.
The websites give guarantees and also portray their 'imaginary' happy customers so as to trick a reader. Such tactics are simple but really powerful and serves to their advantage in most cases. This is also why there are thousands of such websites available.
So is Facebook account an 'unbreakable fortress'?

Well, NO. Facebook accounts can be hacked. No online service is foolproof and that is because of the flaws and bugs in their software. There are several ACTUAL hackers in the world who can analyse a website's security and use that against it thus making hacking a reality.
But I'm 100% sure none of them uses these scam and fake websites that claim to do the impossible. You can check out our hacking section to know more.
I'll end the 'lesson' with an idiom, "look before you leap". Focus, think and then follow. In case of any queries or confusions head over to the comments section. Cheers :)
Monday, February 3, 2014
Opening Number Of Websites Using Python
So you just started in python programming, and want to prank your arch nemesis. Here i will teach you how to open any website on his computer using python.
Before you begin download and install python from Here
Step 1:
open notepad and type
In python the "import" statement is used to add a module to your project. In this case we want to add the webbrowser module.
Step 2:
This is calling the open function on your default web browser. You pass it an url in the form of a string.
Possible usages:
You can add as many websites as you want like show below
The complete code will look something like below
Step 3
Save the file as visus.py
Enjoy pranking your friends and if you wish to learn more programming then check out our article below.
 About Guest Blogger
About Guest Blogger
Cordell Wildermuth is a young blogger. He loves Blogging on high quality secutiy and hacking tutorial. He is currently running his security blog infosmuggler
Before you begin download and install python from Here
Step 1:
open notepad and type
import webbrowser
In python the "import" statement is used to add a module to your project. In this case we want to add the webbrowser module.
Step 2:
webbrowser.open('http://SITE HERE!.com')
This is calling the open function on your default web browser. You pass it an url in the form of a string.
Possible usages:
You can add as many websites as you want like show below
webbrowser.open('http://coolhackingtrick.com')
webbrowser.open('http://google.com')
url = "http://coolhackingtrick.com";
webbrowser.open(url)
The complete code will look something like below
import webbrowser
webbrowser.open('http://coolhackingtrick.com')
webbrowser.open('http://google.com')
webbrowser.open('http://yahoo.com')
webbrowser.open('http://facebook.com')
Step 3
Save the file as visus.py
Enjoy pranking your friends and if you wish to learn more programming then check out our article below.
Cordell Wildermuth is a young blogger. He loves Blogging on high quality secutiy and hacking tutorial. He is currently running his security blog infosmuggler
Friday, January 31, 2014
How Does The Free Services And Softwares Can Cost High?
Of course it is awesome to get something totally free of cost, isn�t it? But are you aware that the free thing can cost you much more in near future. How? Let us study. Many of the service and softwares are sold free of cost just to populate it in a large number of people. Some �business minded� individuals thought that it would be �cool� to add some advertisements to such applications to earn money. As �Excess of anything is bad�, too much of greed and rise in difficulty in advertising led to the birth of adware and spyware.
Adware is type of malware, which misleads, corrupts and harasses the users by popping out unwanted or irrelevant advertisements. They sometimes consist of viruses and Trojans. While the spywares, justifying its name, spies on the user�s activities and online behaviour and reports to the concerned person.
How bad they can be?
Adwares and spywares being malware can affect you and your website or system to a greater extent.- They can help intruders add viruses and Trojans into website and system.
- They can help other malwares to be injected into your website and system.
- Can slow down your website/system�s performance.
- Clashes with other softwares and tools.
- Help hackers gain access to your credentials.
- Can result in to theft of your valuable data and sometimes even money.
- If you are an adware-spyware victimized website, you may become the source of spreading the viruses and Trojans and hence can get blacklisted and ultimately can lose reputation.
How can you prevent being a victim?
Now, that you aware regarding the ill-effects of the adwares and spywares, you should be cautious while exploring the Internet.Following points will help you keep a safe distance from adwares and spywares:
- Avoid visiting on suspicious website: Don�t get into those websites which is not trustworthy or is famous or experienced as a spreader of malwares. Stay away from Piracy; often the pirated softwares contain viruses and Trojans (avoid sites like warez).
- Don�t click on the pop-ups and other ads: Never get drifted away by the pop-ups and ads especially those asking �click here� or �Yes or No� even asked while installing the software.
- Give a little test to pass: Softwares like Spychecker can help you out to find whether the software you are going to install is bugged with a spyware or not.
- Secure your system: Install anti-virus softwares and keep them updated. They will help you around detecting the viruses and Trojans and will also help remove them.
- Use Firewall: Firewall helps prevent entry of hackers and will always ask permission before allowing any traffic to enter. As in the case of Adware and spyware they definitely need to deliver their information collected and with Firewall on, you can successfully stop them doing so.
- Scan your website/system: Get a malware/adware/spyware scanner installed. Scanning will not only help you detect the injected malicious substance but also removes them, if found any. Ad-Aware is one such program.
Security is very sensitive matter for both the IT service providers and users. One should proceed very carefully. As for the IT service providers like software publishers, website owners, e-commerce website owners, e-mails service providers and so on should install SSL certificate for better performance and uninterrupted growth.
For users, well, always look for two symbols �https� and a green padlock in the address bar. Download softwares from the real authors only and stop propagating piracy.
Tuesday, January 28, 2014
Hackers Outside Hollywood - How Hacking Really Began?

Before Hollywood took the hacking phenomena under its wing, unless you were a clued-in techy, the world of hacking would be unfamiliar territory. In recent years, movies like The Girl with the Dragon Tattoo, The Matrix and The Italian Job have managed to glamourize the high-tech thrill of breaking into servers, cracking door codes and hijacking security networks.
But before television brought the hacker technology into our general knowing, hacking was still an occurring reality for some. So what is the history of hacking and where did today's sophisticated hacking begin?
Late 1950s � The MIT Start Off with a Bang
Hacking wasn�t always about computers. In fact, the first �hackers� were roof and tunnel hackers, which the Massachusetts Institute of Technology was instrumental in introducing. These were people who entered roof and utility tunnel spaces without authorization, in other words getting into a place they shouldn�t be in � which is where computer hacking got its name when people started using technology to get into data systems they shouldn�t have access to!
Roof and tunnel hacking was initially intended as practical jokes and saw the hanging of banners from tall places and the popular placing of a model car on the top of a university building. Unsecured entry points would be used to gain access and cause mischief as per the desire of the hacker.
Early 1970s � The Era of Phone Phreaking

�Phone Phreaks� were committed to gaining unauthorized access to telephone systems, which quickly saw the evasion become a criminal offence.
Mid 1970s � A New Level of Virus Sophistication is Met
In 1975, several Motorola staff unearthed a way to crack the security system on the Xerox machine using a simple programming strategy. They reported the problems as a matter of urgency to Xerox but when no action was taken to resolve the loophole, Motorola staff mischievously installed programs named Robin Hood and Friar Tuck.
These programs were designed to cause mischief in the system such as printing insulting messages to each other or making huge old disk drives �walk� across the floor, and the programs prevented the system operator from aborting them by protecting each other and persistently reappearing after rebooting of the system.
2007 � The Return of Urban Exploration
The 1950s exploration of physical spaces returned with Parkour and free-running as a more creative mode of accessing abandoned and forbidden places. Parkour involves running, jumping, swinging and vaulting over obstacles in the hope of trespassing � all in the name of creativity and freedom, and all, technically, a form of �hacking�.
The Present Day � 'Information wants to be free'

It seems that with the advancements in technology and the evolving of hacking with time, we can anticipate a nightmare future of computer hacking. Prevailing hackers are likely to turn their attention to governmental projects and entering mainstream security systems by clever impersonation. Computer coding has become child's play for many and it is anticipated for budding hackers to seek opportunities to enter the world of biohacking, where even the software of life and our DNA itself remains unsafe!
What do you think will be next in the world of hacking?
Gregg Townsend is passionate about everything from gadgets to web-design and likes to keep up to date with the latest news regarding hacking. Connect with him here on Twitter.
Friday, January 17, 2014
How To Remove All Your Google Web History?

In this post, I'll show you how to remove your entire Google web history.
Before we begin, please note that any data you remove will be deleted permanently. Google keeps a lot of useful information that helps you find what you're looking for faster. It gives you quick access to webpages you've visited in the past, and even lets you know in search results which pages you've visited, and when. This information can be useful if you're a power user, and like to get things done quickly.
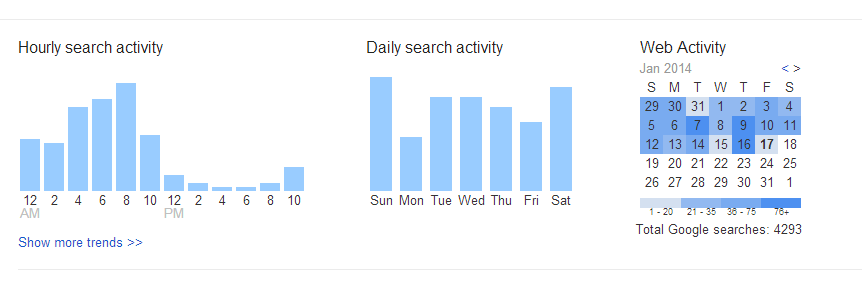
But if you still want, you can go ahead and erase your entire web history. You can also pick and choose individual items to remove, so that you won't lose everything.
Delete your Google Web History
Follow these steps to partially or completely.- Step 1: Visit your Google History page at https://www.google.com/history. Alternatively, you can click the gear icon
on the upper right corner of a search results page, and then go to Search history.
- Step 2: Click on the gear
icon again, and then go to Settings.

- Step 3: Click on the delete all link. You'll be prompted for a confirmation. Click on Delete all again, and your entire search history is gone!

- Step 4 (optional): Click on the Turn off button on the Settings page to stop Google from storing your history again
If you don't want to delete your entire history, you can select individual items from the History main page, and delete them. This, by no means, implies that Google has nothing more to do with your data. They still keep some of your information on their servers for auditing and other such purposes. But at least your personal data is off the line now, and isn't susceptible to leaking out into the wrong hands.
Rest easy :)
Subscribe to:
Posts (Atom)

























